
- Atgfw
- Business Security
- Cloud based service
- Cyberbullying
- Cybersecurity
- Phishing
- Phone System
- Security System
- Servers
- Uncategorized



How an MSP Strengthens Your Business’s Cybersecurity Posture

Cybersecurity is no longer optional—it’s a necessity. With threats like ransomware, phishing, and data breaches on the rise, businesses must take a proactive approach to security. But should you handle cybersecurity in-house or partner with a Managed Service Provider (MSP)?
1. Do You Have the Budget for an In-House Cybersecurity Team?
Hiring and maintaining an in-house cybersecurity team requires significant investment in salaries, training, and cutting-edge security tools. MSPs provide enterprise-grade security at a predictable cost, making cybersecurity more affordable without sacrificing quality.
2. Can Your Business Handle 24/7 Threat Monitoring?
Cyber threats don’t follow business hours. If your company lacks the resources for round-the-clock monitoring and rapid incident response, an MSP ensures constant protection, identifying and stopping threats before they escalate.
3. Are You Prepared for Compliance & Regulatory Requirements?
Industries such as finance, healthcare, and e-commerce must follow strict cybersecurity regulations (e.g., GDPR, HIPAA, PCI-DSS). MSPs specialize in compliance management, ensuring your business meets legal requirements and avoids costly fines.
4. Do You Have the Right Security Tools & Expertise?
Cybercriminals continuously evolve their tactics, and keeping up requires advanced security solutions like intrusion detection, endpoint protection, and AI-driven threat analysis. MSPs provide access to top-tier security tools and skilled experts without the overhead of purchasing and managing them yourself.
5. How Fast Can You Recover from a Cyberattack?
A cyberattack can lead to data loss, system downtime, and reputational damage. MSPs offer disaster recovery and backup solutions, ensuring your business can quickly restore operations and minimize losses.

Key Features of an Ideal MSP
- Offer a flexible service model
- Take a shared approach to managed services
- Have a solid strategic relationship with either your solutions or cloud provider
- Have many consultants available
- Offer advanced services
- Utilize remote monitoring and management for proactive maintenance
- Have a solid backup and disaster recovery strategy
- Have an established escalation path and provide a secondary contact
- Work with your legal team to address compliance issues
The Bottom Line
If your business lacks the budget, expertise, or resources for comprehensive cybersecurity, partnering with an MSP is the smart choice. By outsourcing cybersecurity to professionals, you get 24/7 protection, cost savings, compliance support, and peace of mind, allowing you to focus on growing your business. As cyber threats continue to rise, investing in an MSP is a strategic move that enhances your cybersecurity posture, compliance, and peace of mind.
🚀 Stay Secure. Stay Ahead. Consider an MSP Today! 🚀
Ready to enhance your cybersecurity posture?
🔹Contact Applied Technology today and take the first step towards a more secure future! 🔹

MSP’s to Enhance Business Efficiencies
A Managed Service Provider is a company that offers a range of IT services to businesses on an ongoing basis.
Instead of handling IT tasks in-house, companies outsource their IT needs to an MSP who will proactively manage and support their systems, networks, and technologies. MSPs typically offer services like network management, cybersecurity, data backups, cloud services, helpdesk support, and system monitoring.
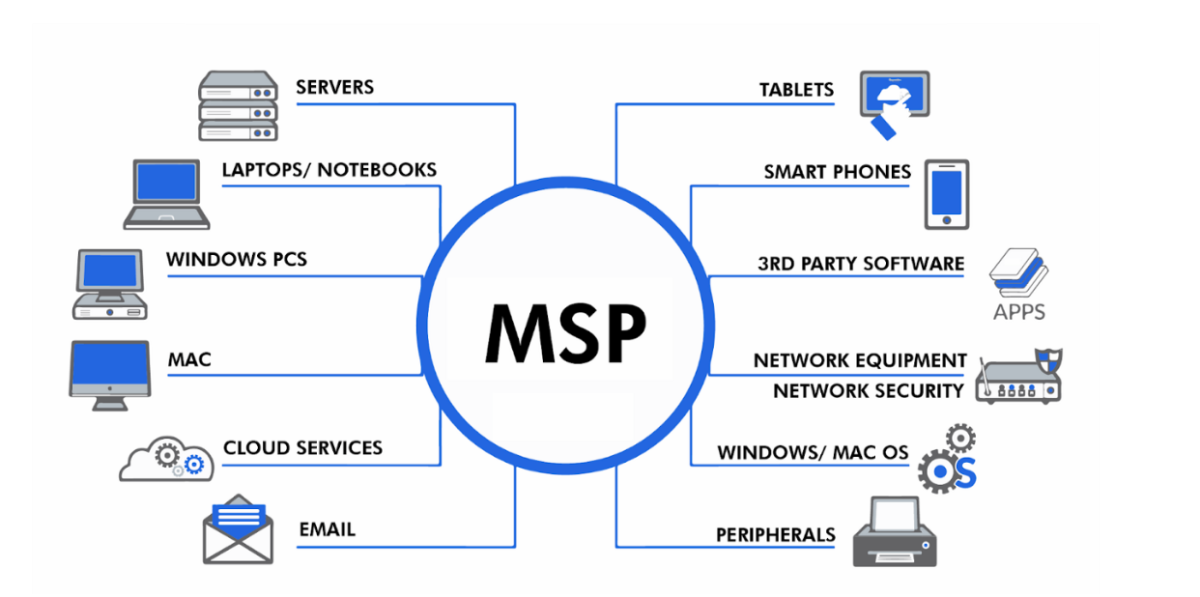
Here’s how an MSP can enhance your business:
- Cost Savings: MSPs provide affordable IT services with a predictable monthly fee, avoiding the need for an in-house team.
- Expertise: Access to specialized knowledge and advanced tools without hiring or training staff.
- Proactive Monitoring: Continuous system monitoring to prevent downtime and resolve issues before they escalate.
- Scalability: Services can easily grow with your business, adapting to new needs.
- Cybersecurity: Robust protection against cyber threats, ensuring data security.
- Focus on Core Business: Free up internal resources to focus on strategic goals instead of tech issues.
- Disaster Recovery: Backup systems and recovery plans to minimize data loss and downtime.
How Using an MSP Works for Your Business:
When you partner with an MSP, they first assess your current IT setup and identify areas for improvement. They’ll then implement tailored solutions to fit your specific business needs. Ongoing support and maintenance are part of the package, so you don’t have to worry about tech issues disrupting your operations. With a dedicated team managing your IT, your business can run more efficiently, securely, and without the stress of dealing with tech problems. The MSP acts as an extension of your business, providing continuous support to help your company grow and evolve.
Overall Statement:
By leveraging the expertise of an MSP, businesses can offload their IT management, ensuring systems are secure, up-to-date, and running smoothly. This allows them to focus on growth and innovation, rather than getting bogged down by technical challenges, leading to increased productivity, reduced risks, and long-term success.
Ready to take your business to the next level?
Let us handle the tech while you focus on what you do best. Reach out to us today at sales@atgfw.com or call 260-482-2844.
We’re here to help you grow!

Implementing MFA: A Layered Approach to Securing Data
What Is MFA and How Is It Different from 2FA?
Multi-factor authentication (MFA) is a security process requiring two or more verification factors to gain access to a system. It’s an enhancement of two-factor authentication (2FA), which typically combines two elements (e.g., password + a one-time code). MFA goes further, allowing for three or more factors, such as biometric data or behavioral analysis, for an additional layer of security.
Why Implement MFA?
MFA significantly reduces the likelihood of unauthorized access by adding layers of verification beyond passwords, which are vulnerable to phishing and breaches. Businesses use MFA to protect sensitive applications, data, and systems, especially for remote or traveling employees who connect from varied locations.
For example, a traveling employee accessing company files from a hotel Wi-Fi network is a prime target for cybercriminals. Without MFA, a stolen password could lead to a full system compromise. With MFA, even if a password is stolen, the attacker would still need a second (or third) factor—like a hardware key or fingerprint—to gain access.
Best Practices for Implementing MFA:
- Select Reliable MFA Methods:
Use secure options like:- Hardware security keys (e.g., YubiKeys)
- Biometric authentication (e.g., fingerprint or facial recognition)
- Push notifications through secure apps (e.g., Microsoft Authenticator or Duo).
- Avoid Weak MFA Methods:
Avoid SMS-based authentication, as text messages can be intercepted through SIM-swapping or phishing attacks. - Ensure Compatibility:
Choose solutions that integrate seamlessly with your existing tools and workflows. - Educate Employees:
Train your staff on the importance of MFA and how to use it effectively.
MFA is a critical investment to protect your business in today’s evolving cybersecurity landscape. Ensure your data stays safe by implementing robust, layered defenses.
PRO TIP
Check to see whether your email accounts, banks, healthcare providers, and other important accounts offer MFA and enable it by default. If they don’t, ask them why not. It’s your information they’re putting at risk!
Take Action Today!
Your company’s security is more than a simple password. Implementing MFA is a vital step toward safeguarding your business. Let Applied Technology Group help you create a secure, layered defense strategy tailored to your needs. Contact us today at Sales@atgfw.com or 260.482.2844 to get started.
“Passwords vs. AI Hackers: Your First Line of Defense in 2025”
In a world where AI hackers never sleep, your best weapon is preparation.
In 2025, advanced AI hackers are pushing cybersecurity to the brink. A strong password is your first line of defense in this digital arms race. Protecting your data starts with mastering the basics: strong passwords. Here’s why they matter and how to stay ahead:
- AI Hackers Are Smarter Than Ever: Machine learning enables them to guess weak passwords in seconds, exploiting simple combinations like “123456” or “password.”
- What Makes a Password Strong:
- At least 12 characters long.
- A mix of uppercase letters, lowercase letters, numbers, and symbols.
- Unique for every account—no repeats!
- Leverage Tools for Extra Security:
- Use password managers to generate and store complex passwords.
- Enable two-factor authentication (2FA) to create an additional security layer.
- Avoid Common Mistakes:
- Don’t use personal info (birthdates, pet names, etc.).
- Steer clear of dictionary words or predictable patterns like “abc123.”
Don’t let AI hackers catch you off guard, because when it comes to cybersecurity, it’s better to be paranoid than sorry!
Partner with Applied Technology Group for robust cybersecurity solutions that safeguard your data, accounts, and peace of mind. From password management to comprehensive security strategies, we’ve got you covered.
📞 Contact us now to learn how we can help protect your organization against evolving threats 260.482.2844 | Sales@atgfw.com.
Let’s secure your future together!

Social Media Scams
Scammers have always taken advantage of people’s trust and social media platforms have only made it easier for them to do so. One of the most well-known examples of this is the Tinder Swindler, who uses the dating app to manipulate unsuspecting individuals.
The scam works by creating a fake profile and establishing a relationship with the target. This is done by building trust through friendly conversation, eventually leading to the scammer asking for personal information or money. This can take the form of a crisis situation or an emotional plea for help.
Unfortunately, social media scams are becoming increasingly common. According to a report by the Better Business Bureau, reports of social media scams have increased by over 450% in the past three years. This shows just how effective scammers have become at exploiting people’s trust through these platforms.
To protect themselves, individuals need to be aware of these scams and take steps to verify the identity of those they meet online. This can be done by doing research on the person’s background, using reverse image search on their profile picture, or checking their social media profiles.
In conclusion, scammers like the Tinder Swindler exploit a fundamental aspect of human nature – trust – to manipulate individuals through social media platforms. With the rise of these types of scams, it is crucial for individuals to be cautious and take steps to protect themselves. By being aware and vigilant, individuals can avoid falling victim to these scams and keep their personal information and money safe.
Harnessing AI for Marketing Automation & Productivity
The integration of artificial intelligence (AI) presents an unparalleled opportunity to optimize marketing strategies and enhance overall efficiency. Below we have highlighted six ways companies can utilize AI, emphasizing how harnessing its capabilities can lead to streamlined processes, optimized resource utilization, and ultimately, increased operational efficiency.
- Automated Copywriting: AI-powered tools can revolutionize the process of creating compelling copy and content. AI platforms can generate coherent and engaging text, saving you valuable time in crafting marketing materials. While AI can provide a creative starting point, it’s crucial to review and refine the content to align with your brand’s voice and messaging.
- Campaign Ideation: AI can assist you in brainstorming and generating innovative campaign ideas. By analyzing market trends, customer behaviors, and historical data, AI tools can propose effective strategies that resonate with your target audience. Human expertise should guide the final selection of campaigns, ensuring they align with your business goals.
- Data-Driven Insights: AI can help to extract valuable insights from large datasets, assisting you in understanding customer behavior, preferences, and market trends. Utilizing these insights can inform strategic decision-making, allowing you to tailor your marketing efforts for maximum impact.
- SEO Assistance: AI tools play a crucial role in optimizing search engine visibility. They aid in keyword research, content optimization, and competitor analysis, helping you enhance your online presence. However, human oversight is essential to ensure that content aligns with the overall marketing strategy and maintains a genuine connection with the audience.
- Social Media Scheduling: AI can analyze data to determine the best days and times to post on social media for maximum engagement. Automated scheduling tools can ensure that your content reaches the audience at optimal moments. Try and balance automation with real-time engagement and community management to maintain authenticity.
- Chatbots for Customer Service: Implementing AI-powered chatbots can significantly improve customer service efficiency. These bots handle routine queries, providing instant responses and freeing up human resources for more complex tasks. However, it’s crucial to design chatbots with a seamless transition to human support when needed, ensuring a positive customer experience.
Things to Remember:
- Exercise caution in accepting responses at face value. While tools like ChatGPT can offer comprehensive answers, they might not always deliver accuracy. Always fact-check responses and cross-verify information from other sources.
- Never share sensitive information. Remember that AI platforms cannot guarantee privacy or security. Sharing sensitive business or personal information may pose identity theft or fraud risks.
- Don’t rely solely on AI. While these tools can be a valuable resource, avoid making significant decisions based solely on its responses. It lacks the ability to understand context and emotions.
- Use AI as a starting point. It is tempting to rely on AI to handle document drafting entirely. While it’s a valuable resource for direction and initial drafts, it lacks the human touch and intuition necessary for certain business documents.
- Avoid generating harmful content. AI models, being devoid of moral judgment, can generate content influenced by biased or harmful data. To avoid this, ensure the data that you input is diverse and representative.

End-of-Year Technology Checklist: Ensure a Smooth Transition into the New Year
As we approach the end of the year, it’s the perfect time to ensure that your business’s technological landscape is poised for a successful transition into the upcoming year. To facilitate this, we’ve compiled a comprehensive checklist that will guide you in wrapping up the year on a technologically sound note. Some items on this checklist will require collaborative efforts, while others will be the responsibility of your team.
Items We’ll Tackle Together:
1. Asset Inventory:
Conduct a thorough review of your technology assets, covering hardware, software, and networking equipment. Keep your inventory list updated to reflect any additions or retirements throughout the year.
2. Password Security:
Implement multi-factor authentication for critical systems and applications to enhance password security across your organization.
3. Software Updates:
Ensure all software applications, operating systems, and antivirus programs are up to date with the latest patches and updates for optimal performance and security.
4. Data Backups:
Verify the functionality of your data backup systems and test the restoration process to ensure a seamless recovery of essential data in case of a disaster.
5. Security Assessment:
Conduct a Security Risk Assessment to identify and address potential vulnerabilities, ensuring your cybersecurity measures are up to date against evolving threats.
6. Employee Training:
Mandatory cybersecurity training for employees to reinforce best practices and raise awareness about potential threats.
Items for Your Team’s Action:
1. Subscription Reviews:
Review and audit all software and service subscriptions to align them with your business needs. Cancel any unnecessary subscriptions to optimize costs.
2. Budget Review:
Evaluate your technology budget for the year, identifying areas where adjustments may be needed for the upcoming year.
3. Technology Roadmap:
Develop or update your technology roadmap for the coming year, aligning it with your business goals and objectives.
4. Compliance Check:
Ensure that your technology practices comply with industry regulations and standards applicable to your business.
5. Communication Plan:
Communicate any upcoming changes or upgrades to your team to ensure a smooth transition without disruptions.
Once you’ve determined your goals and budget, we propose a meeting to discuss the implementation plan for any changes. If you have questions or need assistance, our support team is here to help at Support@atgfw.com. We’re committed to helping you navigate the year-end process and ensuring a seamless start to the new year.
Wishing you a successful year-end, and we look forward to supporting your technology needs in the coming year!

Protecting Your Business: Defending Against the Rise of AI-Driven Scams
In today’s rapidly evolving digital landscape, ensuring the security of your business is more crucial than ever. Recent advancements in artificial intelligence (AI) have brought about new threats, particularly in the form of AI-related scams. These scams, especially those utilizing voice technology, present substantial risks to both individuals and businesses. As a responsible business owner or manager, it’s essential to stay informed and take proactive measures to protect your enterprise from these evolving dangers.
Voice scams, powered by AI technology, involve malicious actors impersonating trusted individuals or entities through voice manipulation. These scammers often target sensitive information or even initiate financial transactions under the guise of a familiar and trusted voice. The increasing sophistication of these scams necessitates a proactive approach to fortify your business’s security measures.
Understanding the Risks and Taking Precautions
Protecting Your Business
Safeguarding your business from voice scams and other AI-related threats requires a multi-faceted approach:
1. Verification Protocols: Establish stringent verification procedures for requests involving sensitive information or financial transactions, especially those communicated via voice. Implement a process that involves multiple verification steps to validate the authenticity of the request.
2. Employee Training: Educate and remind your team about the risks associated with voice scams. Stress the importance of verifying any unusual or sensitive requests, even if they appear to come from familiar sources.
3. Secure Communication Channels: Emphasize the use of secure, encrypted communication channels for the exchange of sensitive information within your organization and with external parties. Implement tools and technologies that prioritize data security.
4. Regular Updates: Keep your security software updated, including anti-phishing and anti-malware tools, to defend against the evolving landscape of AI-driven threats. Regular updates help fortify your defense against the latest scamming techniques.
5. MSP Support: Your Managed Service Provider (MSP) is a key ally in navigating these security challenges. They can assist in implementing robust security measures and provide guidance on staying protected against AI scams. Don’t hesitate to seek their support and expertise.
Commitment to Your Business’s Security
As your trusted partner, we are committed to helping you navigate the challenges posed by these emerging threats. We understand the critical role security plays in maintaining the stability and success of your business. Our aim is to ensure that your enterprise remains secure, enabling you to focus on your core operations without the looming threat of scams and breaches.
If you have any concerns, questions, or need assistance in strengthening your security protocols, please reach out. We are here to support you and your business’s safety is our utmost priority.
Conclusion
In the digital age, the landscape of threats is constantly evolving. AI-driven scams, especially voice scams, present a growing challenge that requires proactive measures to counter. By implementing robust security protocols, educating your team, and leveraging the support of experts in the field, you can significantly fortify your business against these emerging risks.
Remember, your safety and the security of your business are of paramount importance to us. Let’s collaborate to ensure a secure and prosperous future for your enterprise.
Stay vigilant and secure.
