
jacobw
Posts by Jacob Wagner:
- Atgfw
- Business Security
- Cloud based service
- Cyberbullying
- Cybersecurity
- Phishing
- Phone System
- Security System
- Servers
- Uncategorized


Be Cyber Aware: If You Connect It, Protect It
Be Cyber Aware: If You Connect It, Protect It
In today’s age, we all must be cyber aware. The average American today has access to more than 10 Internet Connected Devices in their household. Most have at least 2 computers and 2 smartphones. Across the world, an estimated 30 billion+ devices connect to the Internet. This connectivity generates massive potential for advancement; but in turn, creates a paradise for hackers. This is nothing new as hacking has been on the rise since the dawn of connected technology. And here is the problem. Most businesses have maintained the same security protocols for just as long. The theory is that what they’ve done so far has worked, so why is there any reason for change? Here are the seven reasons why technology is more dangerous than ever before:
- Let’s Be Cyber Aware About Ransomware
The first computer virus was introduced in the 1970s. It took over systems by replicating on the hard drive until the user did not have system space to operate. It was built as an experiment and had no malicious intent/implications. Today, viruses are not child’s play or experiments, and the most dangerous attacks take over the hard drive completely, encrypting every piece of data. If you are connected to a network, it can then infiltrate the servers and start encrypting there. If your data backups are also on that network, you lose all access to a clean backup. The only way to get this data back is paying the ransom or working with an IT company to revert to a clean data/decrypt the files based on the specific ransomware in play. Either way, you’re spending a lot of money and time to get back what’s yours to begin with, your precious data.
- Part of Being Cyber Aware is Knowledge of Phishing
Phishing emails at one time were super easy to spot. Since then, we have become more cyber aware, but phishing attempts have improved. Today, phishing attempts are a whole lot smoother. The perpetrator does enough research to identify your boss, then sends an email under his/her name asking you to discretely transfer money or send identifying financial information. Unless you’re looking at the exact email address it’s coming from (typically spoofed by one or two letters in the domain), all of a sudden, you’ve transferred $40,000 into an unknown person’s account thinking it’s your CEO.
You won’t think anything of it until you speak with your CEO later and realize that it wasn’t really them. These honest mistakes cost companies hundreds of thousands of dollars every year with very little recourse to get the money back where it belongs. Some experts say that employee mistakes cause nearly 92% of breaches.
- Insider Threats
As more people work remote, particularly with the urgency of the past year, businesses have lost tight control on their data, increasing the threat of malicious insiders. While we want to trust every person working for us, that one disgruntled employee who decides to store a copy of the customer data before putting in his two-week notice, could wreak havoc on your business when they decide to work for your closest competitor. Virtual Office solutions can alleviate a lot of the pain this could cause and allow you to keep every piece of data exactly where it belongs.
- Data Leaks and Password Practices
You may be wondering how a LinkedIn password breach can really hurt you in the long run (after all they just gain access to your professional resume). 53% of people admit to reusing their password on multiple accounts. Hackers rely on this. They can sell the password or utilize that password to hack much more dangerous things, like your banking institution. Our best recommendations: use complex passwords, don’t reuse passwords, use a password vault to keep track of all your passwords, and implement two-factor authentication wherever you can.
- Become Cyber Aware About Cryptojacking
Cryptocurrency is a hackers’ favorite payment method. It is untraceable and extremely valuable. Beyond requiring cryptocurrency for most ransomware attempts, some hackers infiltrate a system and use it to mine cryptocurrency without the user’s knowledge. They get in utilizing a malicious email link or through malvertising (advertising that carries nefarious code). A user may recognize slightly slower performance, but they more than likely never know that someone is using their system to mine cryptocurrency. Some codes also spread throughout networks, so that hackers can maximize their financial gain using someone else’s resources.
- IoT Hacks
As we connect more devices to the Internet, particularly those items in our homes – stoves, cars, Alexa, or Google – we open another target for hackers to infiltrate our lives. They may canvas homes through your connected camera system or baby monitor, install viruses on your stove or vehicle that impact performance, or begin speaking to you randomly from your device. IoT can be safe, but you must make sure you’re utilizing as many security precautions as humanely possible.
- Hacker Advancement
The greatest advantage for hackers is they have become more sophisticated and educated overtime, and the good guys haven’t been able to keep up. If you’re relying on internal IT or an MSP without security expertise, your team is most likely behind on the threats and not implementing everything they need to keep your staff safe. They should implement things like phishing tests, employee education, dark web scanning, hosted back-up solutions, crisis planning, multi-factor authentication, and professional-grade permissions control for administrative privileges to keep you safe. If you’re unsure of your security level with your current IT solution, contact us.

Benefits of a Newer Phone System
Phones have come a long way since Alexander Graham Bell in 1876. Over the nearly 150 years since that first phone call was made by Bell, phones have evolved exponentially. In this article, we are going to discuss the latest in business phone communication and some benefits to be had by making the switch from a cabinet–based phone system, to a more modern software-based solution.
The first benefit of a software–based system is reliability. Software makes up most of the system, decreasing the chance of hardware failure. This also makes it much easier to provide a redundant system in the rare occurrence of a failure.
A second benefit is the ability to scale the phone system more easily than a digital system. Like mentioned above, the system is a software-based PBX which limits the amount of hardware necessary. What this means for scalability is adding additional phones/users or additional features no longer requires hardware upgrades to the system. Whereas on a digital system, there is a hard limit to the quantity of phones the system could hold before needing to purchase more hardware. Often those limits are in smaller quantities such as 16 phones. That makes the cost for the 17th phone much higher.
A third benefit is the accessibility of the phone system. With older digital phone systems, the only access you have is the physical phone on your desk. With a newer system you would have access from a physical desk phone as well as a web client and even a cell phone app. The web client can be used as a soft phone with a headset accessed through the internet. The cell phone app allows you to take and make calls from your cell phone as if you were in the office. No longer would you have to give out your cell phone number to clients.
These are just a few highlights of the many benefits of a software-based system. If you would like to hear more about other features, or talk more in-depth about the benefits above, we would love to have that discussion with you. Give us a call at 1-833-TECH-033 or email us at info@atgfw.com.

Degree of Awareness
This week we are sharing a true story about a girl named Jane who is a college-aged student and who is applying for jobs. Jane is in graphic design and has a portfolio, so when she came across a well-known company that creates sports-branded gear that was hiring, it was something she wanted to pursue. She sent them her portfolio electronically, and they set up an interview using a chat forum. They asked a few questions and then asked her to fill out forms that were going to put her in the queue to receive work from them. She completed each one and recommended this to friends, who were all excited about this opportunity that would give them income, experience, and work on a contractor basis.
Until one of her friends paused as he was asked to give his social security number, his address, date of birth, banking information for payments rendered, and so on.
You can see where this is going. They were hackers and they had just been handed Jane’s entire identity by merely dangling a carrot of opportunity in front of her.
Most of us are probably thinking how can you possibly think that a job interview is conducted over a chat room? How can you hand over so much information without questioning what they need it for? Or without even questioning if it is legitimate? Think about this – Jane is a young adult in her early twenties, she is intelligent, she is not careless, and she has worked two jobs. The point is she is a responsible adult that fell victim to a cybersecurity attack just like thousands and thousands of other adults.
It is also safe to say that these days many people would not question anything about interacting entirely online, never meeting face to face, or even via video. Electronic communication is the norm and oversharing is all part of the game too, so why would it be strange to have a job interview any other way? She was trying to find a way to provide income and gain experience. Hackers know our weaknesses; they know how to gain our trust and they customize their attacks based on the audience. You think you know what you would do, but that is because you can see things clearly from the outside when you aren’t the target. When you are in it, you are less likely to see it so obviously. Humans are after all, only human. As we work to protect our homes, our businesses, our identity, and our families let’s remember that smart cybersecurity is like a streaming account – everyone is going to have a different profile but still be using the same platform. Yet the commonality among all of it is that humans are the weak link that will inevitably be the way a cybercriminal gets in the door.
Do you wonder if you or your staff are making the same mistakes Jane is making? Is it possible that hackers have your data? Click here to get more information or to schedule your free assessment.

Cyber Security Trends for 2021
Bell bottoms, neon colors, kale. Trends come and trends go, and generally, at Applied Technology Group, we’re not one to care much about what’s in style, but cybersecurity trends? That’s one we can get behind and think that there can never be enough of!
So, what can you expect to see as a consumer, employee, employer, business owner or just a member of the general public who has a computer? Let’s take a look at what we are seeing.
Home is where the heart is.
And it is where the school is, and the office, and unfortunately it is where the likelihood of an attack or breach happens as well. That means that you need to ready your home and prepare to not only protect but also respond in the event of your network or smart devices being compromised. Ensure that as a worker or student, you are well protected and working with your IT support staff to have all security measures in place. As an IT provider, you must do the same for yourself and those that you support. It will not be easy since many of us are playing catch up to the unexpected transition from last year to work from home scenarios, but it will be of the utmost importance as we move forward with this being the structure for the foreseeable future.
Inside Job
There is a horrible phenomenon that is growing in popularity known as insider-threat-as-a-service. Yes, you can buy a disgruntled employee to sabotage a business and compromise data integrity by stealing information or breaking the business from inside. While this has been around for longer than 2021, with the hiring process for remote employees being done via video or other long-distance methods, it isn’t always easy to gather and gain the trust you might have had from years of sharing office space.
Fake ID
Stolen credentials can be used for more than obtaining a credit card. Yes, you can build up an identity and establish credit, but you can take it a step further and build up a history that doesn’t exist in reality to the person it is being created for. This is a step up from the insider job that can happen, but you do need to be aware of who you are hiring and providing your confidential information to.
Bigger Phish
With humans being the biggest risk to cybersecurity and working from home being the norm, you can expect a rise in attacks. Why? Because humans are the easiest point of entry for any hacker, and unmonitored humans are even easier to trick. So phishing scams will be even more popular when it comes to attack attempts. You can mitigate your risks by using a training program like our simulated phishing emails.
The bottom line with any trend is that it will increase and decrease in popularity over time, but the one trend that isn’t going anywhere is the threat of data breaches. While the outfit or the outward appearance may change, it is always worn on in an attempt to disguise the true identity.

Our update regarding COVID-19 (Coronavirus)
We know COVID-19 (coronavirus) continues to be a large concern for many of you – just as it is for all of us here at Applied Technology Group. Our thoughts and prayers are with those directly affected by the virus and we are grateful to those who are working tirelessly to treat them.
We want you to know that Applied Technology Group is taking proactive measures to ensure that we will be able to continue to support our partners whether we are in the office or working remotely. We have made sure that our staff has everything they need to continue to provide support, no matter where they are, with as little disruption as possible.
There are many factors that must be considered with remote working. If you need help getting your company setup for remote work, please contact us immediately. We have solutions that can help with the transition to remote working. For many of our clients, the solutions we have in place will already support remote workers. We encourage you to reach out to our support teams if you have any questions or concerns.
You can reach our support teams at the following email addresses:
For IT related questions: itsupport@atgfw.com
For telephone system related questions: voicesupport@atgfw.com
For security related questions: security@atgfw.com

Tech bit: Dangers of NOT Upgrading Windows 7 & Server 2008
TO UPGRADE OR NOT TO UPGRADE?
SHOULD YOU GET RID OF WINDOWS 7 AND SERVER 2008? WHAT IF YOU DON’T SWITCH?
On January 14, 2020, Microsoft will end its support for Windows 7 and Server 2008. But just because you can continue to use Windows 7 after the end of life date, it doesn’t mean you should. Businesses who rely on technology to keep them running are proactively upgrading their Windows environment to avoid downtime, user issues, poorer functionality and increased security vulnerabilities.
Businesses who remain on Windows 7 and Server 2008 will be left behind with:
- No technical support
- No software updates
- No security updates
Businesses who do not upgrade might think they are saving some money now, but may have a far bigger and more expensive problems coming.
Windows 7 end of life countdown:


END OF LIFE IS COMING.
Don’t get caught without support. Update your operating system and server before time runs out for Windows 7 and Server 2008.
WHAT DOES THIS MEAN FOR SECURITY?
Procrastinating the upgrade will leave your company’s systems weak and vulnerable to data breaches, liability issues and other cyber threats. Any new vulnerabilities will remain vulnerable. Operating systems and servers need to be continually updated to stay secure. Without updates, patches, and bug fixes, your environment will be exposed to cybercriminals who will exploit vulnerabilities.
Not upgrading your Windows environment will expose your company to external threats. Hackers are waiting for companies who don’t migrate from Windows 7 after the end of life date and are no longer supported or secure. Don’t be tempted to try to save a bit of money and be at risk for a situation that is preventable… because it could end up costing an unpredictable amount!
WHAT DO YOU NEED TO DO? MAKE PLANS TO UPGRADE FROM WINDOWS 7 AND SERVER 2008.
You now know that Windows 7 and Server 2008 will not be a safe product to use after January 14, 2020. If you haven’t already done so, it’s time to start preparing your business to get upgraded. For businesses, we recommend using an IT professional, like us, to ensure everything is working properly and upgraded correctly.
- Develop a budget & plan to replace or update your computers and servers before 2020.
- Call us for an inventory evaluation.
- Act now…time is moving fast and we want to help you before it’s too late.
If you don’t know where to start, we’re here to help. As a trusted technology adviser, we are actively helping companies upgrade their Windows environment with a seamless process and affordable rates to accommodate their budget and time frame. Contact us today to see how we can help you transition your Windows environment to be more secure and better protect your business.

Tech Bit: Windows 7 EOL
 Currently, there are a few options to choose from when it comes to Windows 7 EOL. Don’t be tempted to go to Windows 8. Though it is a newer version, it’ll only be a matter of time before you need to migrate all over again. You should transition to Windows 10. Depending on when you purchased your computer, you might be eligible for a free upgrade to Windows 10.
It’s important to begin working on this migration as soon as possible. Please reach out to us so we can take a look at the devices you are using, determine how many are utilizing Windows 7, and ensure your hardware isn’t out of date. Not all computers will be able to handle a new operating system, which could make a migration take much longer, more difficult, and costlier as you upgrade hardware. We will provide a recommended path for an upgrade with a clear budget and timeline for completion.
Currently, there are a few options to choose from when it comes to Windows 7 EOL. Don’t be tempted to go to Windows 8. Though it is a newer version, it’ll only be a matter of time before you need to migrate all over again. You should transition to Windows 10. Depending on when you purchased your computer, you might be eligible for a free upgrade to Windows 10.
It’s important to begin working on this migration as soon as possible. Please reach out to us so we can take a look at the devices you are using, determine how many are utilizing Windows 7, and ensure your hardware isn’t out of date. Not all computers will be able to handle a new operating system, which could make a migration take much longer, more difficult, and costlier as you upgrade hardware. We will provide a recommended path for an upgrade with a clear budget and timeline for completion.
Overall, take some time to plan your transition. Talk to us if you need additional help or options. Most of all though, get moving now. EOL will be here in no time.
(featured image rights to TDM Group)

Tech Bit: Phishing Pt. 2
Credential Stealer – An attacker will make a convincing clone of an existing webpage such as a Google account login screen or Facebook login screen. The idea behind this clone of a webpage is to have a victim enter their credentials (username/password) giving the attacker access to their account. Some popular examples of this attack are account verification, sharing files on the cloud, and package delivery. All of them revolve around receiving an email marked with apparently legitimate indications it is from a real company or organization such as Amazon, Google, or UPS. All 3 examples share the same purpose of luring you to enter your login information giving access to the hackers.
Malicious attachments – In our Increasingly technology-based world, it is more likely that companies you use regularly will contact you via email. Examples such as your bank, Google, or even your anti-virus service providers. This gives hackers a whole new opportunity to attack you based on specific services you use. Hackers create emails nearly identical to the ‘Credential Stealer’ emails, with one major difference: They come with a malicious attachment. These attachments may include fake reviews of your recent bank activity. Once you click to the see your bank activity in this malicious attachment your computer can be infected with viruses or malware.
Credential Stealers and Malicious Attachments are just two attack methods. Targeting methods used by hackers include the following:Vishing – Refers to phishing done over phone calls. Since voice is used for this type of phishing, it is called vishing → voice + phishing = vishing.
Smishing – The user is targeted by using an SMS (short message service) alert.
Search engine phishing – Refers to the creation of a fake webpage for targeting specific keywords and waiting for the searcher to land on the fake webpage.
Spear Phishing – Unlike traditional phishing, which involves sending emails to millions of unknown users, spear phishing is typically targeted in nature, and the emails are carefully designed to target a particular user.
Whaling – Similar to spear phishing, expect whaling targets a more specific and confined group. Whaling is more focused on “landing the whale” and targeting higher level executives, while with spear phishing anyone from the top or the bottom of the company is at risk.
Phishing schemes will continue to develop and update as does the surrounding technology, but there are ways to prevent the attacks described above:The most significant thing you can do to ensure your business is taking the correct steps against phishing attacks is working with a trusted MSP. With how impossible it may seem to stay up-to-date with threats regarding technology is where your MSP should step in and be your knowledgebase for technology. Phishing prevention and protection requires a multi-layered solution. A full stacked solution can consist of a plethora of things such as scans, phishing tests, monitoring, and much more. These solutions can be custom tailored to fit your business as no business is 100% the same as another. Phishing hackers won’t care whether you are a small or large business. They will target their victims without discrimination.
Like any other security risk, it’s better to act proactively to phishing rather than reactively. Contact us today at (260) 482-2844 to begin the process of tailoring a solution specifically for you.
Our simple process to get your business secure:1. Discovery – An initial meeting to learn more about your organization and what you do.
2. Assessment – Our engineers examine your network and policies to learn how to best project you.
3. Implementation – We deploy our solution designed specifically for your organization followed by exceptional ongoing service.
Thank you for reading!
Citations:
Preethi. “14 Types of Phishing Attacks That IT Administrators Should Watch For.” SysCloud Blog, 8 Jan. 2019, blog.syscloud.com/types-of-phishing/.
Slavin, Brad. “Top Phishing Email Attacks Worldwide in 2018.” DuoCircle, 12 Feb. 2019, www.duocircle.com/phishing-protection/top-phishing-email-attacks-worldwide-in-2018.
Wright, Jordan. “The Trouble with Phishing.” Duo.com, Duo Security , 2016.
Click below for part 1 on Phishing

Tech Bit: Phishing pt. 1
Network security’s importance continues to grow with the ever-evolving technology industry. Ensure your network is secure ahead-of-time instead of waiting until disaster strikes. Protecting the IT infrastructure within your business increases the reliability and safety of the business. Threats to your business can come in forms such as viruses/malware, phishing attacks, password attacks, or a denial-of-service (DoS) attack, and new attacks are being created regularly. All of these will cause more than just a headache for your IT department and could end up costing your business time and money.
Phishing is one of the most common threats hitting organizations. A phishing scam is when an email is sent in an attempt to get a response in order to gain information; such as a username and password. Phishing works because email, like physical mail, is built to assume that the sender is whom they claim to be.
Typically, the scammers will attempt to create a great amount of fear or panic in a potential victim by saying things such as “an attempt to login to your email was made from some [insert random city] click this link below to reset your password”. When someone reads that tag line from an email and sees legitimate looking aspects to the email, such as a Google logo displayed on it, they are more likely to believe it without even checking the website address.
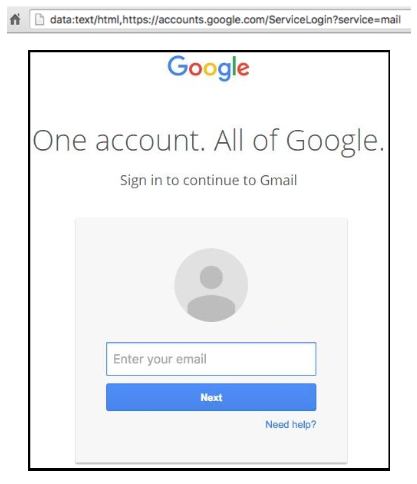
Phishing is common because it is easy to create these fake emails and it has continued to grow in recent years. According to Webroot, a company that specializes in end-point protection, over 1.5 million new phishing sites are created each month. Since a clear majority of phishing attempts come through email, anyone with an email account is a potential target for these attacks. Just because you have not been targeted yet does not mean you never will.
Here are a few things to keep in mind if you don’t believe the effectiveness of a phishing scam attempt:
• According to Cybersecurity Ventures, a world leading research group in the global cyber economy, Ransomware damages are now predicted to cost the world $11.5 billion in 2019, and $20 billion in 2021.
• According to Intel, 97% of people around the world are unable to identify a sophisticated phishing email.
• According to Cisco, 31% of people click the phishing links. Cisco saw that 17% of users enter their credentials into the phishing site as well.
Again, these attacks happen because they work. Phishing is effective because of how easy it is to send out massive amounts of emails. Sending large amounts of emails significantly increases the odds of someone clicking the link and entering their information.
Want to learn more about phishing? Give us a call at 260.482.2844 and make sure you keep an eye out for more information as this is just part 1 of our 2-part blog posts on phishing. Part 2 will go more in-depth over the specific types of attacks that people are using and what steps you should take to protect your business.
Thank you for reading!

 Facebook
Facebook Linkedin
Linkedin