
loris
Posts by :






How an MSP Strengthens Your Business’s Cybersecurity Posture

Cybersecurity is no longer optional—it’s a necessity. With threats like ransomware, phishing, and data breaches on the rise, businesses must take a proactive approach to security. But should you handle cybersecurity in-house or partner with a Managed Service Provider (MSP)?
1. Do You Have the Budget for an In-House Cybersecurity Team?
Hiring and maintaining an in-house cybersecurity team requires significant investment in salaries, training, and cutting-edge security tools. MSPs provide enterprise-grade security at a predictable cost, making cybersecurity more affordable without sacrificing quality.
2. Can Your Business Handle 24/7 Threat Monitoring?
Cyber threats don’t follow business hours. If your company lacks the resources for round-the-clock monitoring and rapid incident response, an MSP ensures constant protection, identifying and stopping threats before they escalate.
3. Are You Prepared for Compliance & Regulatory Requirements?
Industries such as finance, healthcare, and e-commerce must follow strict cybersecurity regulations (e.g., GDPR, HIPAA, PCI-DSS). MSPs specialize in compliance management, ensuring your business meets legal requirements and avoids costly fines.
4. Do You Have the Right Security Tools & Expertise?
Cybercriminals continuously evolve their tactics, and keeping up requires advanced security solutions like intrusion detection, endpoint protection, and AI-driven threat analysis. MSPs provide access to top-tier security tools and skilled experts without the overhead of purchasing and managing them yourself.
5. How Fast Can You Recover from a Cyberattack?
A cyberattack can lead to data loss, system downtime, and reputational damage. MSPs offer disaster recovery and backup solutions, ensuring your business can quickly restore operations and minimize losses.

Key Features of an Ideal MSP
- Offer a flexible service model
- Take a shared approach to managed services
- Have a solid strategic relationship with either your solutions or cloud provider
- Have many consultants available
- Offer advanced services
- Utilize remote monitoring and management for proactive maintenance
- Have a solid backup and disaster recovery strategy
- Have an established escalation path and provide a secondary contact
- Work with your legal team to address compliance issues
The Bottom Line
If your business lacks the budget, expertise, or resources for comprehensive cybersecurity, partnering with an MSP is the smart choice. By outsourcing cybersecurity to professionals, you get 24/7 protection, cost savings, compliance support, and peace of mind, allowing you to focus on growing your business. As cyber threats continue to rise, investing in an MSP is a strategic move that enhances your cybersecurity posture, compliance, and peace of mind.
🚀 Stay Secure. Stay Ahead. Consider an MSP Today! 🚀
Ready to enhance your cybersecurity posture?
🔹Contact Applied Technology today and take the first step towards a more secure future! 🔹

MSP’s to Enhance Business Efficiencies
A Managed Service Provider is a company that offers a range of IT services to businesses on an ongoing basis.
Instead of handling IT tasks in-house, companies outsource their IT needs to an MSP who will proactively manage and support their systems, networks, and technologies. MSPs typically offer services like network management, cybersecurity, data backups, cloud services, helpdesk support, and system monitoring.
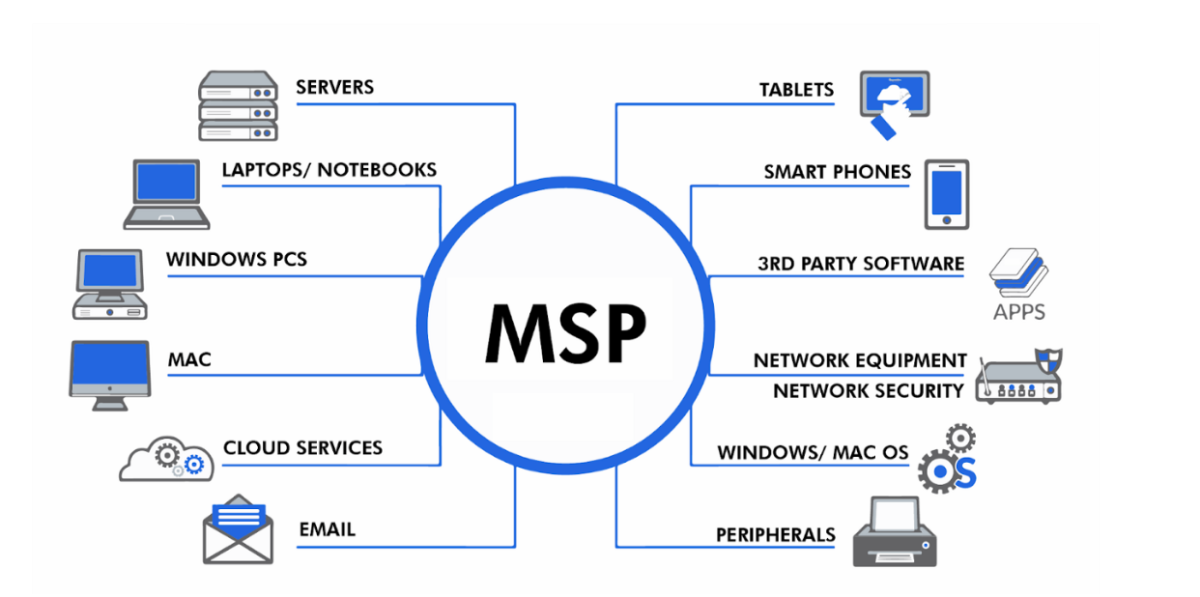
Here’s how an MSP can enhance your business:
- Cost Savings: MSPs provide affordable IT services with a predictable monthly fee, avoiding the need for an in-house team.
- Expertise: Access to specialized knowledge and advanced tools without hiring or training staff.
- Proactive Monitoring: Continuous system monitoring to prevent downtime and resolve issues before they escalate.
- Scalability: Services can easily grow with your business, adapting to new needs.
- Cybersecurity: Robust protection against cyber threats, ensuring data security.
- Focus on Core Business: Free up internal resources to focus on strategic goals instead of tech issues.
- Disaster Recovery: Backup systems and recovery plans to minimize data loss and downtime.
How Using an MSP Works for Your Business:
When you partner with an MSP, they first assess your current IT setup and identify areas for improvement. They’ll then implement tailored solutions to fit your specific business needs. Ongoing support and maintenance are part of the package, so you don’t have to worry about tech issues disrupting your operations. With a dedicated team managing your IT, your business can run more efficiently, securely, and without the stress of dealing with tech problems. The MSP acts as an extension of your business, providing continuous support to help your company grow and evolve.
Overall Statement:
By leveraging the expertise of an MSP, businesses can offload their IT management, ensuring systems are secure, up-to-date, and running smoothly. This allows them to focus on growth and innovation, rather than getting bogged down by technical challenges, leading to increased productivity, reduced risks, and long-term success.
Ready to take your business to the next level?
Let us handle the tech while you focus on what you do best. Reach out to us today at sales@atgfw.com or call 260-482-2844.
We’re here to help you grow!

Implementing MFA: A Layered Approach to Securing Data
What Is MFA and How Is It Different from 2FA?
Multi-factor authentication (MFA) is a security process requiring two or more verification factors to gain access to a system. It’s an enhancement of two-factor authentication (2FA), which typically combines two elements (e.g., password + a one-time code). MFA goes further, allowing for three or more factors, such as biometric data or behavioral analysis, for an additional layer of security.
Why Implement MFA?
MFA significantly reduces the likelihood of unauthorized access by adding layers of verification beyond passwords, which are vulnerable to phishing and breaches. Businesses use MFA to protect sensitive applications, data, and systems, especially for remote or traveling employees who connect from varied locations.
For example, a traveling employee accessing company files from a hotel Wi-Fi network is a prime target for cybercriminals. Without MFA, a stolen password could lead to a full system compromise. With MFA, even if a password is stolen, the attacker would still need a second (or third) factor—like a hardware key or fingerprint—to gain access.
Best Practices for Implementing MFA:
- Select Reliable MFA Methods:
Use secure options like:- Hardware security keys (e.g., YubiKeys)
- Biometric authentication (e.g., fingerprint or facial recognition)
- Push notifications through secure apps (e.g., Microsoft Authenticator or Duo).
- Avoid Weak MFA Methods:
Avoid SMS-based authentication, as text messages can be intercepted through SIM-swapping or phishing attacks. - Ensure Compatibility:
Choose solutions that integrate seamlessly with your existing tools and workflows. - Educate Employees:
Train your staff on the importance of MFA and how to use it effectively.
MFA is a critical investment to protect your business in today’s evolving cybersecurity landscape. Ensure your data stays safe by implementing robust, layered defenses.
PRO TIP
Check to see whether your email accounts, banks, healthcare providers, and other important accounts offer MFA and enable it by default. If they don’t, ask them why not. It’s your information they’re putting at risk!
Take Action Today!
Your company’s security is more than a simple password. Implementing MFA is a vital step toward safeguarding your business. Let Applied Technology Group help you create a secure, layered defense strategy tailored to your needs. Contact us today at Sales@atgfw.com or 260.482.2844 to get started.
