Atgfw




How an MSP Strengthens Your Business’s Cybersecurity Posture

Cybersecurity is no longer optional—it’s a necessity. With threats like ransomware, phishing, and data breaches on the rise, businesses must take a proactive approach to security. But should you handle cybersecurity in-house or partner with a Managed Service Provider (MSP)?
1. Do You Have the Budget for an In-House Cybersecurity Team?
Hiring and maintaining an in-house cybersecurity team requires significant investment in salaries, training, and cutting-edge security tools. MSPs provide enterprise-grade security at a predictable cost, making cybersecurity more affordable without sacrificing quality.
2. Can Your Business Handle 24/7 Threat Monitoring?
Cyber threats don’t follow business hours. If your company lacks the resources for round-the-clock monitoring and rapid incident response, an MSP ensures constant protection, identifying and stopping threats before they escalate.
3. Are You Prepared for Compliance & Regulatory Requirements?
Industries such as finance, healthcare, and e-commerce must follow strict cybersecurity regulations (e.g., GDPR, HIPAA, PCI-DSS). MSPs specialize in compliance management, ensuring your business meets legal requirements and avoids costly fines.
4. Do You Have the Right Security Tools & Expertise?
Cybercriminals continuously evolve their tactics, and keeping up requires advanced security solutions like intrusion detection, endpoint protection, and AI-driven threat analysis. MSPs provide access to top-tier security tools and skilled experts without the overhead of purchasing and managing them yourself.
5. How Fast Can You Recover from a Cyberattack?
A cyberattack can lead to data loss, system downtime, and reputational damage. MSPs offer disaster recovery and backup solutions, ensuring your business can quickly restore operations and minimize losses.

Key Features of an Ideal MSP
- Offer a flexible service model
- Take a shared approach to managed services
- Have a solid strategic relationship with either your solutions or cloud provider
- Have many consultants available
- Offer advanced services
- Utilize remote monitoring and management for proactive maintenance
- Have a solid backup and disaster recovery strategy
- Have an established escalation path and provide a secondary contact
- Work with your legal team to address compliance issues
The Bottom Line
If your business lacks the budget, expertise, or resources for comprehensive cybersecurity, partnering with an MSP is the smart choice. By outsourcing cybersecurity to professionals, you get 24/7 protection, cost savings, compliance support, and peace of mind, allowing you to focus on growing your business. As cyber threats continue to rise, investing in an MSP is a strategic move that enhances your cybersecurity posture, compliance, and peace of mind.
🚀 Stay Secure. Stay Ahead. Consider an MSP Today! 🚀
Ready to enhance your cybersecurity posture?
🔹Contact Applied Technology today and take the first step towards a more secure future! 🔹

MSP’s to Enhance Business Efficiencies
A Managed Service Provider is a company that offers a range of IT services to businesses on an ongoing basis.
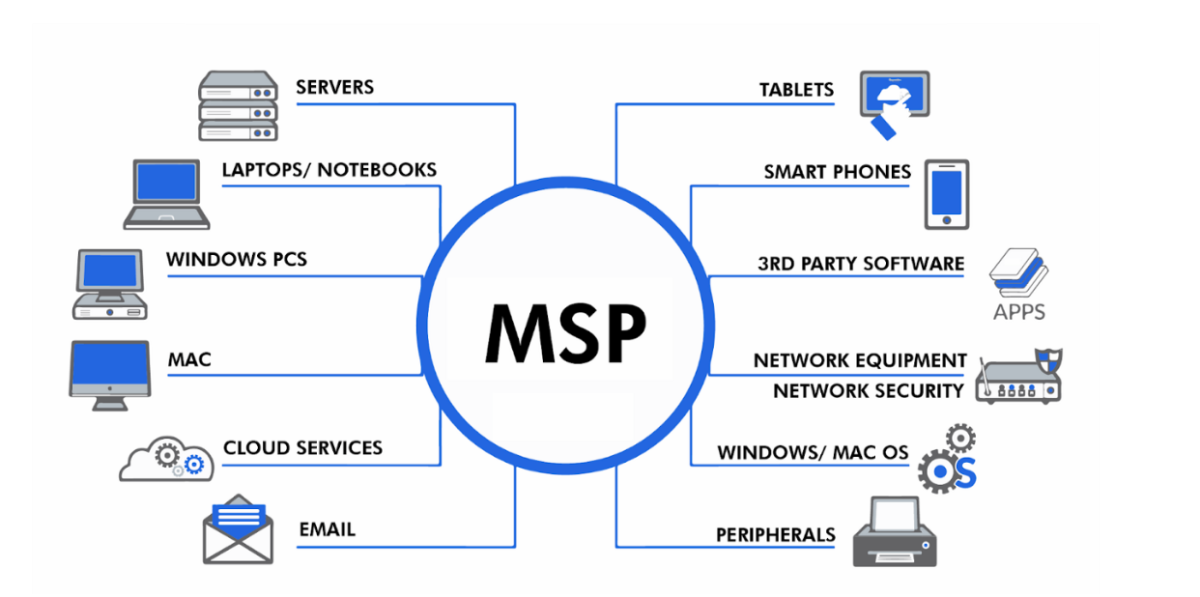
Instead of handling IT tasks in-house, companies outsource their IT needs to an MSP who will proactively manage and support their systems, networks, and technologies. MSPs typically offer services like network management, cybersecurity, data backups, cloud services, helpdesk support, and system monitoring.
Here’s how an MSP can enhance your business:
- Cost Savings: MSPs provide affordable IT services with a predictable monthly fee, avoiding the need for an in-house team.
- Expertise: Access to specialized knowledge and advanced tools without hiring or training staff.
- Proactive Monitoring: Continuous system monitoring to prevent downtime and resolve issues before they escalate.
- Scalability: Services can easily grow with your business, adapting to new needs.
- Cybersecurity: Robust protection against cyber threats, ensuring data security.
- Focus on Core Business: Free up internal resources to focus on strategic goals instead of tech issues.
- Disaster Recovery: Backup systems and recovery plans to minimize data loss and downtime.
How Using an MSP Works for Your Business:
When you partner with an MSP, they first assess your current IT setup and identify areas for improvement. They’ll then implement tailored solutions to fit your specific business needs. Ongoing support and maintenance are part of the package, so you don’t have to worry about tech issues disrupting your operations. With a dedicated team managing your IT, your business can run more efficiently, securely, and without the stress of dealing with tech problems. The MSP acts as an extension of your business, providing continuous support to help your company grow and evolve.
Overall Statement:
By leveraging the expertise of an MSP, businesses can offload their IT management, ensuring systems are secure, up-to-date, and running smoothly. This allows them to focus on growth and innovation, rather than getting bogged down by technical challenges, leading to increased productivity, reduced risks, and long-term success.
Ready to take your business to the next level?
Let us handle the tech while you focus on what you do best. Reach out to us today at sales@atgfw.com or call 260-482-2844.
We’re here to help you grow!

Implementing MFA: A Layered Approach to Securing Data
What Is MFA and How Is It Different from 2FA?
Multi-factor authentication (MFA) is a security process requiring two or more verification factors to gain access to a system. It’s an enhancement of two-factor authentication (2FA), which typically combines two elements (e.g., password + a one-time code). MFA goes further, allowing for three or more factors, such as biometric data or behavioral analysis, for an additional layer of security.
Why Implement MFA?
MFA significantly reduces the likelihood of unauthorized access by adding layers of verification beyond passwords, which are vulnerable to phishing and breaches. Businesses use MFA to protect sensitive applications, data, and systems, especially for remote or traveling employees who connect from varied locations.
For example, a traveling employee accessing company files from a hotel Wi-Fi network is a prime target for cybercriminals. Without MFA, a stolen password could lead to a full system compromise. With MFA, even if a password is stolen, the attacker would still need a second (or third) factor—like a hardware key or fingerprint—to gain access.
Best Practices for Implementing MFA:
- Select Reliable MFA Methods:
Use secure options like:- Hardware security keys (e.g., YubiKeys)
- Biometric authentication (e.g., fingerprint or facial recognition)
- Push notifications through secure apps (e.g., Microsoft Authenticator or Duo).
- Avoid Weak MFA Methods:
Avoid SMS-based authentication, as text messages can be intercepted through SIM-swapping or phishing attacks. - Ensure Compatibility:
Choose solutions that integrate seamlessly with your existing tools and workflows. - Educate Employees:
Train your staff on the importance of MFA and how to use it effectively.
MFA is a critical investment to protect your business in today’s evolving cybersecurity landscape. Ensure your data stays safe by implementing robust, layered defenses.
PRO TIP
Check to see whether your email accounts, banks, healthcare providers, and other important accounts offer MFA and enable it by default. If they don’t, ask them why not. It’s your information they’re putting at risk!
Take Action Today!
Your company’s security is more than a simple password. Implementing MFA is a vital step toward safeguarding your business. Let Applied Technology Group help you create a secure, layered defense strategy tailored to your needs. Contact us today at Sales@atgfw.com or 260.482.2844 to get started.

Small Business Cybersecurity Risks
Cybersecurity Insurance & IT Services
Digital technology continues to evolve which can result in cybersecurity risks. The good news is these changes bring a multitude of new ways that businesses can grow. But along with these developments, there are also the growing risks of online threats. No matter how you try to protect yourself, there will always be a prevailing danger every time you enter the online environment. Even large multinational corporations sometimes become victims of cyber-attacks. So, it’s no challenge to breach small businesses and cause cybersecurity risks.
Addressing Inadequate Security Measures
The good news is those small businesses are not helpless despite the alarming rise in the volume and severity of cyber-attacks in recent years. We can apply several easy but effective steps to mitigate cybersecurity risks. If you look at the most common reasons businesses fall victim to online attacks, it almost always boils down to poor security measures.
For instance, many employees still use weak passwords and have not received training on internet security measures. Many companies use old verification systems or simple authentication methods, leaving their data vulnerable to online attackers.
These are issues that even small businesses can address using an up-to-date cybersecurity strategy. If you don’t have the means to implement this kind of protection, you can always enlist the services of a managed service provider specializing in cybersecurity solutions. We’ll tell you more about this at the end of this blog.
How to Bolster Online Security
If your business gets infiltrated by hackers, it can cost a lot in different aspects. You can lose customers, lose revenue, and experience slow operations. It might even force you to shut down your business in case of customer or vendor data loss. To avoid this trouble, you can take some simple steps right now to bolster online security and prevent online attacks from ruining your business.
Train Your Employees
Most hackers do not directly attack a company’s database or network but go through the weakest path of entry: the employees. Seemingly harmless emails and links might be traps set up by online criminals to get into your system. Every employee must be wary of these suspicious links and know-how to identify possible online threats in various forms.
Update Your System
Technology changes rapidly. The system that once gave you ironclad protection may now be a flimsy wall of defense. Once you miss an update to your system, your entire business will become vulnerable to new malware that hackers have recently developed. It is therefore critical to ensure that your security is always up to date.
Have a Reliable Backup and Recovery Plan
Despite all your protective measures to mitigate cybersecurity risks, you can’t be 100% protected at all times. Therefore, it is vital to have a reliable backup system and quick recovery plan to bring your system back in order in case of an attack. A managed services provider can help you set up a recovery strategy to minimize your losses and get you back into regular operation as soon as possible.
Partnering with an MSP Can Significantly Reduce Your Cybersecurity Risks
Cybersecurity threats will always exist, but there are plenty of ways to defend your business against these threats, like partnering with a dependable Managed Service Provider.

Cyberbullying Prevention
Back to School Cybersecurity: Part 2
While the internet provides endless opportunities for learning, socializing, and self-expression, it also exposes students to various risks. And cyberbullying is one of the most prevalent risks present. As parents or adults with children in our lives, it is our responsibility to create a safe online environment for our children and equip them with the necessary tools to combat and navigate cyberbullying.
Identifying cyberbullying:
- Emotional changes: Keep an eye out for sudden shifts in your child’s behavior, including increased irritability, sadness, anxiety, or withdrawal. These could be indicators of cyberbullying.
- Reluctance to use devices: If your child starts avoiding or becoming anxious about using their devices, it might be a sign that they are facing online harassment.
- Changes in academic performance: Cyberbullying can significantly impact a child’s concentration and academic progress. Notice any unexplained decline in their grades or sudden disinterest in school.
- Social isolation: If your child begins distancing themselves from friends or social activities, it could be due to negative experiences online. Cyberbullying victims often feel embarrassed or ashamed, causing them to withdraw.
- Unusual behavior after using devices: Look for signs of distress, anger, or frustration during or after your child’s online interactions. These behaviors may indicate cyberbullying incidents.
Teaching Kids Not to Participate in Cyberbullying:
- Open communication: Encourage your child to talk openly about their online experiences. Establish a supportive environment where they feel comfortable sharing any concerns or instances of cyberbullying they may witness.
- Empathy and kindness: Teach your child the importance of empathy and treating others with kindness, both online and offline. Encourage them to think about the impact their words and actions can have on others.
- Digital citizenship: Educate your child about responsible digital citizenship. Emphasize the need to respect others’ feelings, privacy, and personal boundaries. Discuss the potential consequences of their online actions and the importance of using the internet positively.
- Lead by example: Be a role model for your child by practicing good online behavior yourself. Show them how to engage respectfully, resolve conflicts peacefully, and use social media and technology responsibly.
- Reporting and seeking help: Teach your child to report any instances of cyberbullying to you, their teachers, or the appropriate platform authorities. Help them understand that seeking help is not a sign of weakness but a step towards resolving the issue.
Remember that you are a role model. Demonstrate positive online behavior and digital etiquette in your own interactions. Avoid participating in or endorsing cyberbullying in any form, and emphasize the importance of empathy, respect, and kindness in both online and offline environments.

Back to School Cybersecurity: A Guide for Parents
Back to School Cybersecurity: Part 1
As another school year approaches, it’s essential for parents to not only focus on buying school supplies and organizing schedules but also on safeguarding their children’s online activities. Cybersecurity is a critical concern, and students can be particularly vulnerable to the risks online. Take proactive steps to educate and protect your child’s online presence, so that you can ensure their safety and provide them with a secure environment for learning.
Here are some practical tips for parents to consider as their children head back to school:
Strong Passwords: Encourage your child to create strong and unique passwords for their various accounts. Teach them about the importance of using a combination of uppercase and lowercase letters, numbers, and special characters. Additionally, advise them not to share passwords with anyone, even their closest friends. Consider using a phrase that may be easier to remember.
Emphasize Online Safety: Remind your child about the significance of privacy while using the internet. Teach them to be cautious about sharing personal information, such as full names, addresses, phone numbers, or school details, on public platforms or with strangers online. Encourage them to think twice before posting anything online and to be aware of potential consequences. For example, saying something like “I can’t play online, I’m on the bus now” gives details about their schedule.
Phishing Lessons: Phishing attempts and online scams can trick even the most vigilant individuals. Explain to your child what phishing emails look like and how to identify suspicious links or attachments. Teach them to be skeptical of messages asking for personal information or requesting money. Reinforce the importance of reporting any suspicious activity to you or their teachers.
Teach Safe Social Media Habits: It is crucial to educate your child about responsible social media usage. Discuss the importance of setting privacy settings to restrict access to their profiles, accepting friend requests only from people they know in real life, and avoiding sharing sensitive information or engaging in cyberbullying.
Install Antivirus Software: Use reliable antivirus software and ensure it is up to date and set to perform regular scans. Explain the significance of keeping software, operating systems, and applications updated to avoid vulnerabilities that hackers may exploit.
Encourage Regular Backups: Save your child’s work on cloud storage platforms or external hard drives regularly. This practice can help them recover their data in case of a cyber incident or device failure.
Communication: Trust and open communication are critical to ensure that your child feels comfortable discussing any cybersecurity concerns they may have. Encourage them to approach you if they encounter any suspicious online activities or receive inappropriate messages. Be supportive and provide guidance without judgment.
Set Boundaries and Time Management: Promote healthy technology habits by setting boundaries on screen time and ensuring your child gets sufficient rest, physical activity, and social interaction. Explain the importance of balance and the potential risks associated with excessive internet use.
As parents, the responsibility to ensure our children’s safety both offline and online begins with us. Have open discussions about cybersecurity, so that you can help protect your child from various online threats. Remember that education and ongoing communication are key to creating a safe digital environment for your child as they embark on another school year. Let’s empower our children to make informed choices and navigate the online world securely.

Fixing Your Weakest Link: Your Employees
Phishing: Part 3
You can have every piece of security hardware in the books: firewall, backup disaster recovery device, and even anti-virus. However, your employees will still be the biggest vulnerability in your organization when it comes to phishing attacks. How do you mitigate as much risk as possible?
- Create and Strictly Enforce a Password Policy: Passwords should be complex, randomly generated, and replaced regularly. In order to test the strength of your password go to howsecureismypassword.com. (This is a perfectly safe service sponsored by a password protection platform that tells you how long it would take a hacker to decode your password.) When creating a password policy, bear in mind that the most prevalent attacks are Dictionary attacks. Most people utilize real words for their passwords. Hackers will typically try all words before trying a brute force attack. Instead of words, use a combination of letters, numbers, and symbols. The longer the password, the stronger it is. While it’s difficult to remember passwords across different platforms, try not to repeat passwords. This will protect all other accounts in the event of a breach on one of your accounts.
- Train and Test Your Employees Regularly: Educate your employees on how they can spot a phishing attack. Then, utilize penetration testing (this is a safe phishing attack orchestrated by your IT company to see how employees respond) and how well they do. If employees fall for phishing attempts then send them through training again. We recommend doing this on a quarterly basis to ensure that your employees stay on their toes and you should provide education on the latest attacks.
- Create a Bring Your Own Device Policy and Protect all Mobile Phones: You can safeguard as much as humanly possible on your network, but your employees are all walking in with cell phones. Are they allowed to get work emails on their phones? What about gaining access to the network remotely? Cell phones create a big black hole in security without proper mobile device management and mobile security.
- Perform Software Updates Regularly: Make sure that your software is up-to-date with all the latest security patches. Holding off on updates means that you’re leaving yourself open to vulnerabilities that have been discovered and addressed.
- Invest in Security: Security is not something for cost savings. Home-based hardware is not sufficient, and you, at the very least need a quality firewall and backup device. Invest in your employee’s training, ongoing security updates, and maintaining a full crisis/breach plan.
There are two things that aren’t going away in any business, employees and security threats. Make sure that you’ve taken care of everything you can to avoid falling victim to these attacks.
